Trapped on Django 3.2? How Enterprises Can Balance Compliance and Migration Reality
From Compliance Risk to Migration Reality: Navigating Django 3.2’s End of Life
Django 3.2 has been the workhorse of enterprise applications for years. As the last long-term support (LTS) version before Django 4.x, it powered mission-critical workloads in finance, healthcare, and government.
However, in April 2024, Django 3.2 reached its end of life (EOL). That means no more security fixes, no upstream patches, and no official support.
For regulated enterprises, that’s more than a technical inconvenience; it’s a compliance risk. Yet for developers tasked with solving the problem, migration is far from trivial.
This guide outlines the compliance landscape and the technical migration realities — so you can strike a balance between both.
Why Enterprises Get Stuck on EOL Frameworks
If you’re reading this as a developer, you already know the pain points:
- Dependency chains: Your app probably relies on dozens of third-party packages. Some may not yet support Django 4.x or 5.x.
- Critical uptime: The systems you support can’t afford extended downtime during migration.
- Breaking changes: Even “simple” upgrades can ripple through URLs, templates, ORM queries, and middleware.
- Organizational priorities: Migration is rarely viewed as a source of “new business value,” resulting in limited resources.
These challenges explain why enterprises get stuck, but they don’t remove the compliance deadlines.
Compliance Risk: Why You Can’t Ignore Django 3.2’s EOL
Django 3.2 hit EOL early in 2024; auditors now view it as unsupported software. That alone can trigger findings across:
- PCI DSS → Patch management requirement = failed if running unsupported software.
- HIPAA → Security Rule expects “reasonable safeguards.” Unsupported software fails that test.
- FedRAMP / NIST 800-53 → Unsupported components not permitted in authorized systems.
- SOC 2 / ISO 27001 → Patch and vulnerability management controls fail.
Even if your app is “stable,” unsupported means “non-compliant.”
Migration Path: Django 3.2 → 4.2 LTS (or 5.1 Latest)
The recommended migration path for enterprises is:
- Django 3.2 → 4.2 LTS (supported until April 2026).
- Plan ahead for 4.2 → 5.2 LTS later (expected in 2026).
While direct migration to Django 5.x is an option, most enterprises will likely favor the stability offered by Django 4.2 LTS.
Hot Spots: Common Breaking Changes (and Who They Impact Most)
Not all Django apps are created equal. Migration complexity is heavily influenced by application size and scope:
- Small Django projects → ~10,000–30,000 lines of code (internal tools, limited dependencies).
- Large Django projects → 100,000+ lines of code (multi-app monoliths, enterprise features, many third-party packages).
If you’re in the latter category, every breaking change multiplies: more code paths to refactor, more dependencies to validate, more test suites to maintain.
Here are the most impactful breaking changes when migrating Django 3.2 → 4.2/5.x — with effort estimates by project size:
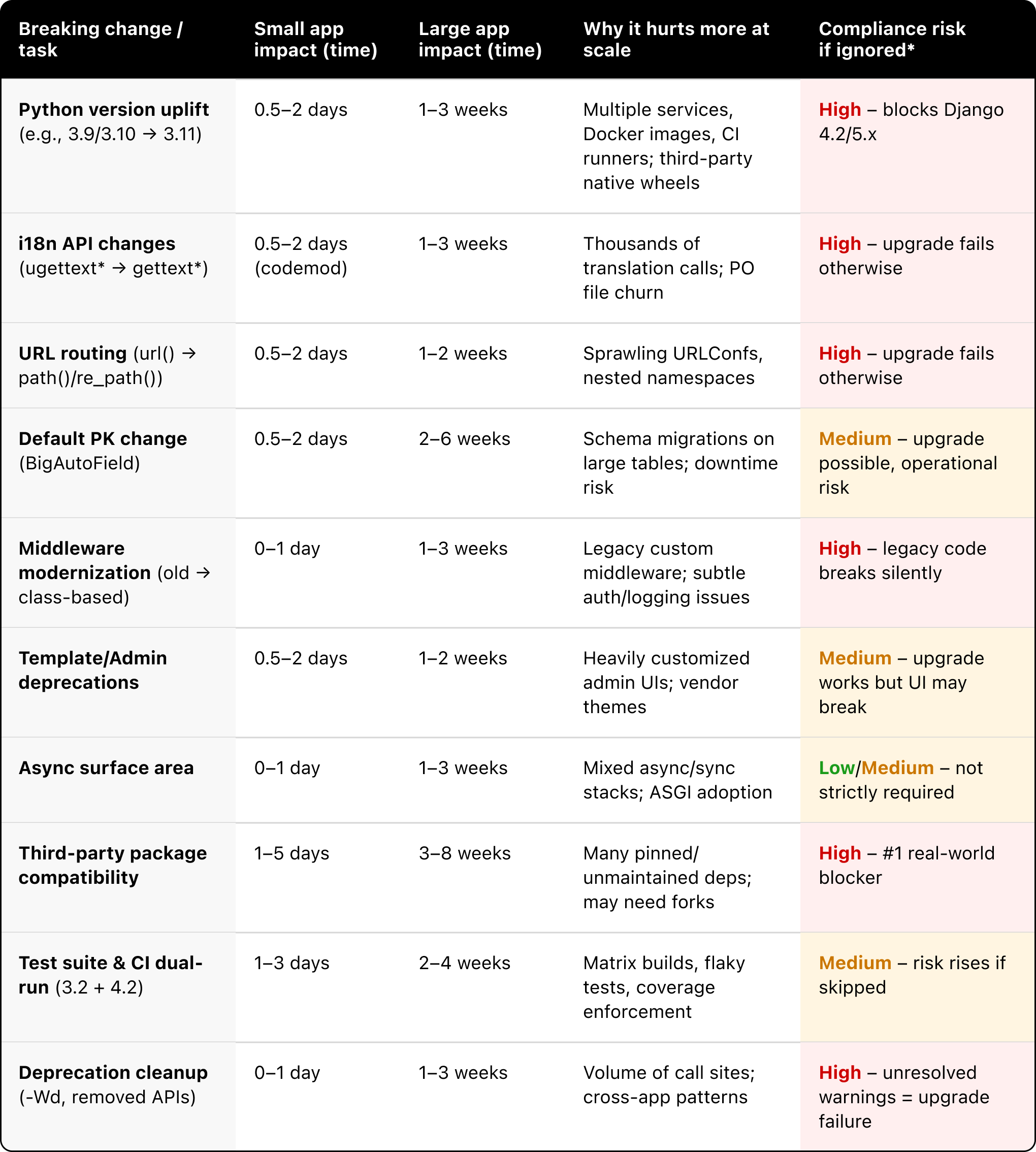
* Compliance risk if ignored means you remain stuck on Django 3.2 (unsupported software) — a common audit finding across PCI, HIPAA, FedRAMP, SOC 2, and ISO 27001.
Rule of thumb for total effort:
- Small Django app (10–30k LOC): ~2–6 weeks of developer effort.
- Large Django monolith (100k+ LOC): ~3–9 months (cross-team effort, staged rollout).
Extended Support: Buying Time When Migration Isn’t Immediate
If migration is blocked by package dependencies or bandwidth, enterprises can look to extended support providers who provide Django security patches beyond official EOL.
- Keeps you compliant with auditors.
- Buys time to plan migrations without rushing.
- Should be treated as a bridge, not a permanent solution.
A Balanced Enterprise Strategy
The most pragmatic approach for regulated enterprises is hybrid:
- Adopt extended support → to cover immediate compliance needs.
- Begin migration planning now → even if execution is staged.
- Communicate cross-functionally → so compliance, dev, and exec teams align on roadmap and risk appetite.
Conclusion
Being “trapped” on Django 3.2 is not unusual — it’s the reality for enterprises with large, regulated systems. But EOL is here, and ignoring it is not an option.
As a developer, you can lead the conversation by:
- Mapping out the real migration blockers.
- Highlighting compliance risks for leadership.
- Proposing a hybrid strategy: extended support now + structured migration plan.
With the right plan, you’ll avoid audit surprises, protect certifications, and ensure your enterprise isn’t left behind on Django 3.2.

.png)
.png)
.png)