Reproducing CVE-2025-55315, the CVSS 9.9 CVE in ASP.NET
Uncover the ASP.NET Core vulnerability (CVE-2025-55315) by reproducing it locally. Here's how to check if your version of .NET is vulnerable and what to do next.

The Threat Posed by CVE-2025-55315
CVE-2025-55315 is a critical vulnerability that involves inconsistent interpretation of HTTP requests in ASP.NET Core and Microsoft.AspNetCore.Server.Kestrel.Core, enabling a sophisticated attack known as HTTP Request Smuggling.
While HTTP Request Smuggling in ASP.NET Core is a moderate-level threat, Microsoft's high 9.9 CVSS score on this CVE reflects a deeper concern, which is the potential impact on applications built on top of ASP.NET Core exploited using HTTP Request Smuggling.
Microsoft assigned a CVSS score of 9.9 out of 10 to CVE-2025-55315, the highest CVE reported on ASP.NET. This score reflects the wide range of vulnerabilities HTTP Request Smuggling could enable in ASP.NET applications.
As highlighted in the Microsoft Security Advisory on GitHub, a smuggled HTTP request could potentially open ASP.NET applications to:
- Injection attacks, allowing an attacker to obtain privileged access on your systems and/or exfiltrate data
- Network requests to arbitrary destinations within your network, such as mapping secured API endpoints
- Escalation of privilege by logging in as another user, allowing exploitation of secured API endpoints
- Being vulnerable to sophisticated phishing schemes, such as performing actions in your application on behalf of users tricked into logging into a phishing site
Remediating CVE-2025-55315
CVE-2025-55315 was reported on .NET 8, 9, and 10, and new builds were released. Users on .NET 8, 9, and 10 should update immediately.
However, .NET 6 is also vulnerable. Because this version has reached end-of -life (EOL) status, no new build or patch is coming. The best way to remediate against post-EOL vulnerabilities in .NET is for users to deploy HeroDevs NES for .NET 6. HeroDevs NES for .NET contains a patch for this and other high and critical vulnerabilities in post-EOL versions of .NET.
We can test if .NET 6 is vulnerable to CVE-2025-55315 by reproducing it directly on an EOL build of .NET 6.
Reproducing CVE-2025-55315 on .NET 6
CVE-2025-55315-repro is a free open source tool we created here at HeroDevs that reproduces the CVE-2025-55315 attack locally and non-destructively. It is a standalone console application based on the functional tests published alongside the upstream patch for CVE-2025-55315. CVE-2025-55315-repro can be run from source or pre-built binaries. You can run it to check if your build of .NET is vulnerable to this CVE.
From Source
To run CVE-2025-55315-repro from source, you must have the .NET SDK 6+ installed. Then run:
git clone https://github.com/sirredbeard/CVE-2025-55315-repro
cd CVE-2025-55315-repro
dotnet build CVE-2025-55315-repro.sln --framework net6.0
dotnet run --project Repro/Repro.csproj --configuration Debug --framework net6.0
Note: Modify the --framework option as needed to match the major version number of .NET you are testing.
Pre-Built Binaries
Binary builds of CVE-2025-55315-repro are available to test .NET 6-10 for Windows and Linux on both x64 and Arm. These can be obtained from ‘Releases’ on the CVE-2025-55315-repro GitHub page. To run CVE-2025-55315-repro from binaries, you must have the ASP.NET Core Runtime installed.
Running CVE-2025-55315-repro
When CVE-2025-55315-repro is executed, it starts a local ASP.NET Kestrel server at http://localhost:5000 and runs two TCP-based tests. The tests send raw HTTP data over TcpClient to exploit chunked transfer parsing and invalid newline handling in ASP.NET.
If the two tests pass, your version of .NET is not vulnerable to CVE-2025-55315. That looks like this:

If the two tests fail, your version of .NET is vulnerable to CVE-2025-55315. That looks like this:
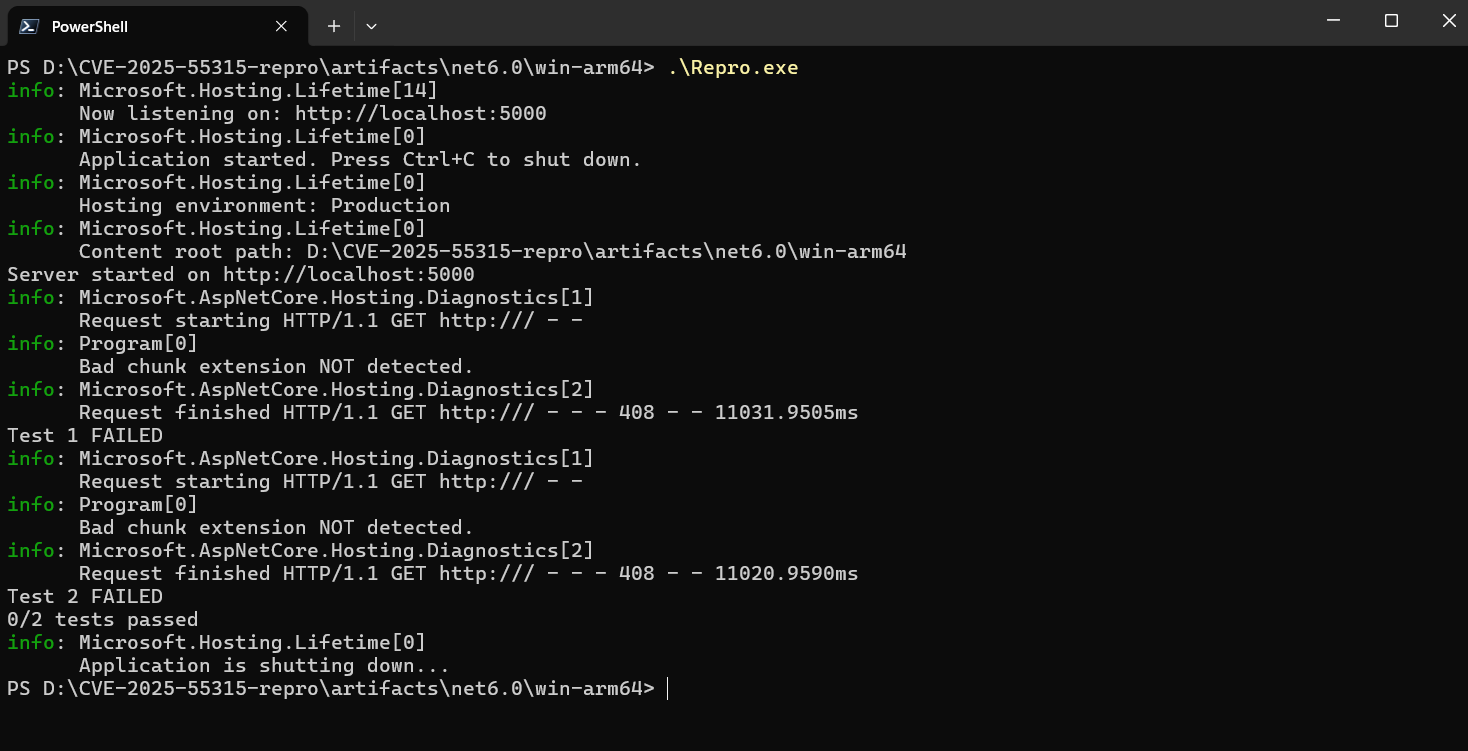
The Undetected CVE-2025-55315 Threat in .NET 6
Microsoft does not report CVEs on EOL software, such as .NET 6, and therefore security scanners and other endpoint management tools may not detect this vulnerability on your systems. However, the absence of a CVE detection does not mean the vulnerability is not present. You can reproduce CVE-2025-55315 yourself on .NET 6 with CVE-2025-55315-repro.
The threat remains and systems running on EOL versions of .NET are still exposed to the risks outlined by CVE-2025-55315, making proactive mitigation or upgrade essential. If you are unable to migrate or upgrade to .NET 8, 9, or 10, you can remediate this CVE immediately with HeroDevs NES for .NET 6.
Proactive .NET Security
Staying proactive with your security updates is the best defense against evolving threats. By upgrading to .NET 8, 9, or 10, or by securing extended support for older versions of .NET with HeroDevs NES for .NET 6, you're safeguarding your .NET applications and your users.

.png)
.png)
.png)